Table of Contents
3 Data Privacy Compliance Challenges that can be solved with OvalEdge
When you manage large amounts of data, privacy will always be front of mind. The most obvious reason is to avoid falling foul of rules and regulations and being heavily fined. But more importantly, you're responsible for protecting your data from third-party threats. Not only for your own sake, but also for your customers and clients.
Although this is widely accepted, it doesn't mean remaining compliant is easy. Countries have multiple laws for data compliance, and different countries have their own variants. And even when countries share laws, like GDPR in Europe, it's always changing and evolving.
Data teams are aiming for multiple goalposts, which are all moving!
Our customers often tell us how much time and effort they are constantly putting in to keep up with regulations like GDPR, CCPA, and IAPP. Which is why data privacy compliance is a key use case we've focused on while building OvalEdge.
In this article, we'll cover the following privacy compliance challenges, and how OvalEdge solves them for you:
- Finding PII data across multiple databases
- Lacking an RTF platform
- Reporting all privacy terms to auditors
Analyze the various aspects of Data Privacy Compliance before revealing how OvalEdge can address them in your company. Download our whitepaper How to Ensure Data Privacy Compliance with OvalEdge
Finding PII data across multiple databases
Problem
You'll struggle to talk about data privacy without talking about personally identifiable information (PII). It's the foundation of the topic, and for good reason. Our personal information, in the wrong hands, can have disastrous consequences.
If a cybercriminal acquires someone's PII, they could do immeasurable damage to a person's financial situation, professional reputation, and personal life. From building up debt, to blackmail, to harassment, it can ruin lives.
It can also have devastating effects on the breached company. They would likely be financially liable, as well as suffering long-term reputational damage.
This is why it's so vital that companies identify the PII elements stored across the entire organization. Not only that, but most major compliance regulations also require businesses to record the complete data lineage.
Often the only way to do this is for developers to read the source code of the software, then document the lineage directly from that. This process can take months, and cost a company a lot of time and money.
Solution
OvalEdge simplifies the inventory process by automatically compiling your data sources into a single data catalog, and uses AI to identify PII across the catalog. You can then mark data as PII, Confidential, or Sensitive, and tag it appropriately.
Users can also quickly browse and locate data using our natural language search. This allows you to manually tag and map PII, using a global business glossary to ensure a standardized approach.
By categorizing and mapping your PII, adhering to regulations, and proving your compliance is a piece of cake. Anyone with access to the data can get a full view, and set up reports and monitoring to remain proactive.
When market-leading freelance platform Upwork struggled to locate all the PII data for their customers, they used OvalEdge to build a data catalog. Connecting all their data sources and using the AI's recommendations, Upwork was able to classify their sensitive data in only a few weeks.
Lacking an RTF platform
Problem
Heavily linked to PII is the Right to be Forgotten (RTF), where if someone asks an organization to delete all their private data, the company is obliged to do so.
This sounds straightforward in theory, but many companies simply don't have the processes or mechanisms in place to carry out this obligation. This puts the business at great risk, as they need to do this to meet GDPR regulations.
The problem is that even if they have a process to submit an RTF request, the data itself is dispersed across multiple systems and databases. Like with identifying PII data, this makes it tricky to find the information you need to delete.
Many organizations simply ignore these regulations, but as more and more people become aware of their rights, hiding your head in the sand won't be an option for much longer.
This is clear when you look at Google's Transparency Report, where they received around 3.2 million RTF requests in the first five years of implementation. And it continues to grow!
Solution
As we've already talked about, OvalEdge identifies personal data by cataloging your entire dataset. Our algorithms are so powerful that they identify this sensitive information with precision.
OvalEdge also automates RTF workflow and processes based on existing compliance precedence. So when you get an RTF request, our advanced algorithm will scan all your data sources, and identify exactly where their personal information is stored.
This makes the process of deleting the data quick and easy. You can then use our advanced data query tools to validate the request and ensure all their data has been removed as requested.
OvalEdge quickly becomes your one-stop-shop for monitoring and implementing RTF, and helps you remain compliant and ethical.
Related: Data Privacy Compliance - How to Ensure it and How it Can Benefit Your Business
Reporting all privacy terms to auditors
Problem
The word 'audit' strikes fear in the hearts of most professionals. It's one thing to create and implement processes, but proving you've done it right is a different monster!
There are a number of reasons to carry out a data privacy audit:
- Find issues that need to be resolved
- Identify where improvements or savings could be made
- Ensuring compliance with regulations
- A client or customer requires it
- It's required to acquire certification
Whatever the reason, you need to be prepared for an audit. It often affects people across the company, and if you're not set up for it, you could fail before you even get started.
Every regulation has different requirements, and you need to know your GDPR from your HIPAA before you even consider allowing an audit to begin.
It's often wise to do an internal audit first, to get an idea of what's working or not. Especially as third-party auditors can be expensive, so you only want them to visit once.
There's a lot to consider, and audit days are often dreaded.
But with the right tools, that needn't be the case...
Solution
OvalEdge gives you centralized reporting, which takes the mystery and headaches out of audits.
You aggregate all your data sources into a data catalog, then you can easily search data, run reports, and manage your data any way you like. You can then present this to auditors in the format they need.
For accurate audits, companies also need to document and map all the movement of their data. This allows auditors to verify that data has only been used ethically and compliantly.
Data governance is another big part of regulation and policy, and with OvalEdge you have strict control over who can access what data. It's also easy to present these access policies to auditors to prove that you're following the policies.
Often this is done by Data Protection Officers, but with OvalEdge you can pick and choose who can access the data, or run reports. Whether that's a nominated colleague, or the auditors themselves.
OvalEdge gives you all the tools you need
Achieving and maintaining compliance with data privacy regulations is pivotal to any company that deals with large amounts of data. You need a tight grasp of the quality of your data, as well as who can access what.
Data is what we care about, and we've built OvalEdge to make this as easy as possible.
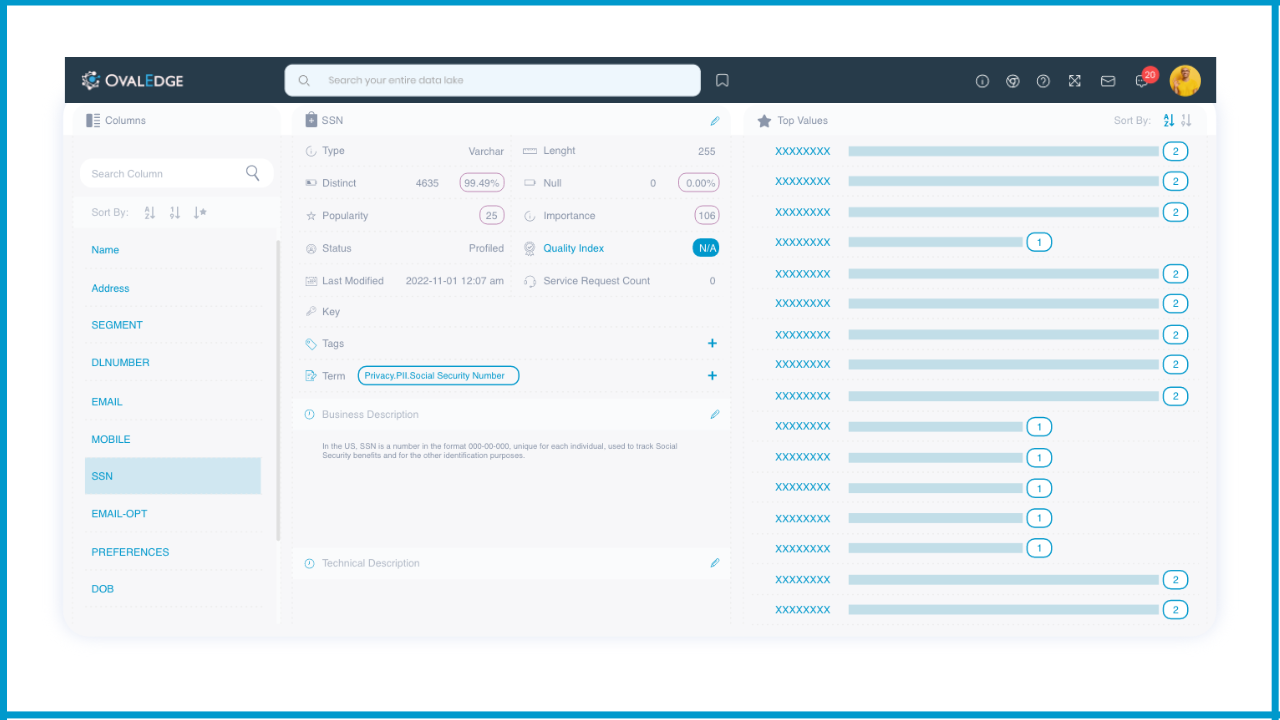
From manually searching for data, to advanced AI, to complex reporting. It can all be done in OvalEdge, giving you the best chance to protect your data, and any other data you access.
This means you don't need to dread audit days anymore, and you can rest easy knowing you're not at risk of regulators banging at your door.
We not only line up your goalposts, but we also stop them moving.
You're welcome!
What you should do now
|